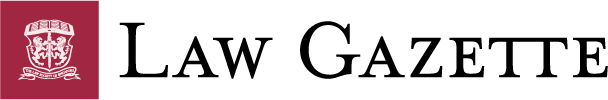Data Risk Management – Why IT Matters
Law Firms – Low Hanging Fruit for Hackers and Scammers
All law firms are vulnerable to data security breaches, regardless of size and location. They are often perceived to be easy targets because law firms handle large volumes of sensitive information and data. And lawyers are generally not known to be tech savvy.
In April and May 2019, two Singapore law firms became victims. The e-mail accounts of their clients, who were property buyers, were hacked. The hackers then posed as their solicitors and requested for fund transfers to complete conveyancing transactions. One of the clients in the two cases fell for the scam, resulting in substantial monetary loss.
The above is an example of a hack and a scam. The hack was the use of technical means to infiltrate and tamper with information in the clients’ computer systems/network. The scam was the use of social engineering to extract monies from the two law firms’ clients – in this case, posing as their lawyers in the conveyancing transactions.
According to the 2019 American Bar Association (ABA) Annual Legal Technology Survey Report on lawyers practising in firms of all sizes, there has been a notable increase in lawyers experiencing some form of security breach.
Common Cyberattacks Against Law Firms
The 2019 PWC Annual Law Firms’ Survey on UK law firms also reported that every respondent to the survey suffered a security incident. The top three attacks were phishing, other incidents caused by staff, and loss or leakage of confidential information.
Phishing
Phishing e-mails invite the recipient to click on an URL link to a website. The attackers masquerade as a trusted entity, often a real or plausibly real person, or a company the recipient might do business with. Once on the website, malware infects the recipient’s computer and all the computers in the network.
Spoofing – Visual confusion
E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from a legitimate source. Because the source appears legitimate, a recipient is more likely to respond. Display name deception and look-alike domain are common spoofing attacks.
Display name deception is often successful as many read e-mails on mobile devices, which only show the display name of the sender.
Attackers also try to deceive the recipient by registering and using domains that are similar to the impersonated domain. Look-alike domain attacks often use homoglyphs or characters that appear similar to the original characters in the impersonated domain. This is easy to miss when one is not alert and rushing to respond to an email.
Data Protection – Make IT Your Priority
 Maintaining the integrity of information that a law firm receives or disseminates is fundamental to managing operational and regulatory risks.
Maintaining the integrity of information that a law firm receives or disseminates is fundamental to managing operational and regulatory risks.
An unauthorised access to a law firm’s IT system not only disrupts business operations and causes reputational damage, it may even result in breaches of data protection and other related regulations.
The Professional Conduct Rules (PCR) 6, 35(4) & (5), require a law firm to take reasonable steps to ensure that the practice has in place adequate systems and policies to protect their client’s money, conflict of interests and client confidentiality.
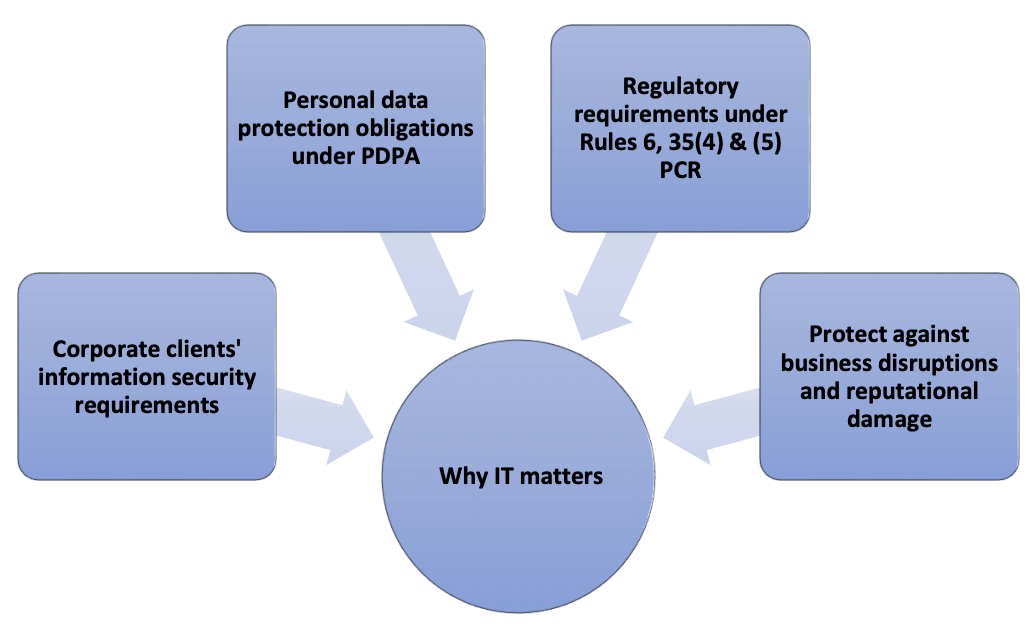
It is compulsory under the Personal Data Protection Act 2012 (PDPA) to appoint a data protection officer (DPO) who is responsible for ensuring the law firm complies with PDPA requirements on collection, usage and disclosure of personal data.
Corporate clients today often require law firms to comply with their information security requirements as part of panel appointment criteria.
Accordingly, a law firm must ensure:
- its IT systems are integrated, reliable and secure;
- it has in place software and hardware cybersecurity;
- it has policies on e-mails, social media and use of its IT equipment; and
- continuing education for employees on cybersecurity.
Data Protection Obligations Under the PDPA – IT is Mandatory
Recently, a law firm was found by the Personal Data Protection Commission (PDPC) to have breached personal data protection obligations when one of its administrative staff mistakenly sent out two e-mails meant for a client to an incorrect address on two separate occasions. A third e-mail was mistakenly sent by the firm’s managing partner with an attachment which wrongly contained the names of two other clients of the law firm.1Matthew Chiong Partnership (2019) SGPDPC (7).
In his decision, the Commissioner highlighted that the law firm and its staff “should be vigilant in its handling of personal data” as it is “in the business of providing legal services, and handles large volumes of personal data on a day to day basis.”
The Commissioner also “advised that suitable checks and controls be implemented before e-mails containing sensitive personal data are sent.” 2Refer to PDPC’s Guide to Preventing Accidental Disclosure When Processing and Sending Personal Data.
The above decision highlights the importance of having in place policies, processes and practices to comply with PDPA requirements.
For guidance on how to develop a systematic framework on data protection and management, refer to PDPC’s comprehensive guide on how to develop a data management programme (DPMP)3Guide to Developing a Data Protection Management Programme.Refer to the PDPA Assessment Toolkit available on the PDPC webpage for guidance on how to conduct data protection risk assessments and implement risk mitigating measures.Also refer to “Why you may need a privacy policy” The Singapore Law Gazette June 2017 for suggestions on how to develop a privacy policy for your law firm.Refer to the Law Society Guidance Note on cloud computing (paras 12,13,15,16 & 17)..
PDPC’s Guide to Developing a Data Management Programme
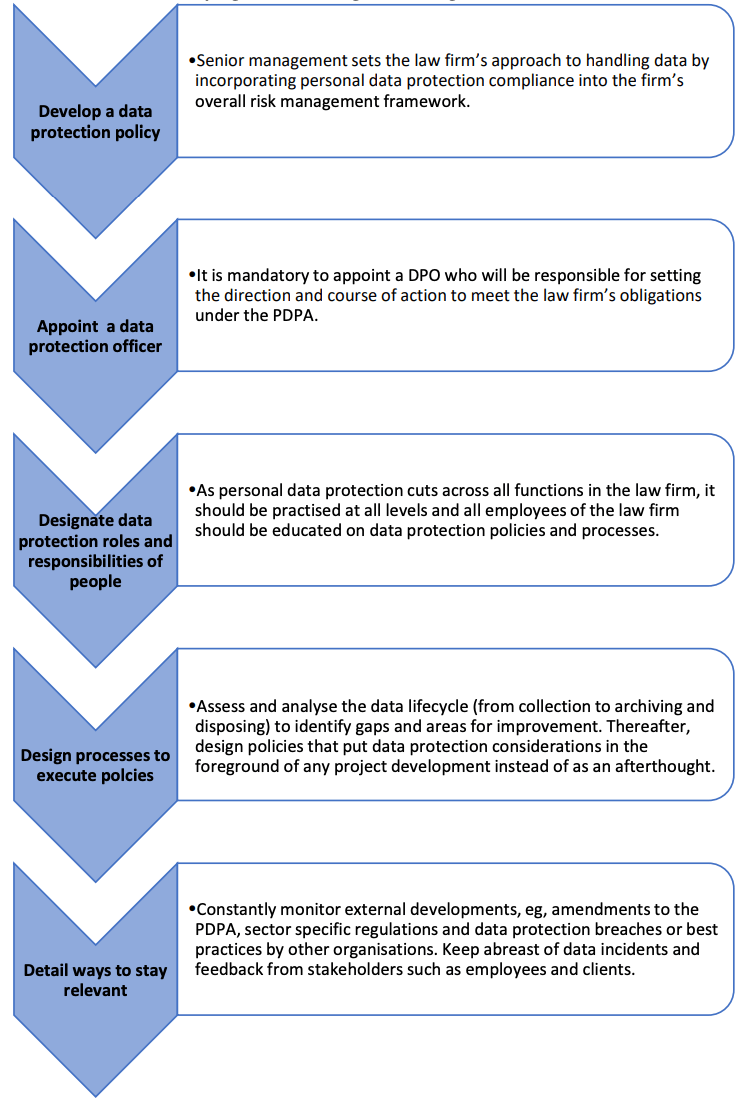 Mitigating Data Breach Risks – IT is Important
Mitigating Data Breach Risks – IT is Important
1. Invest in IT support
Hire technically qualified IT personnel to put in place IT systems that are integrated, reliable and secure.
2. Risk assessment of the firm’s system vulnerabilities
- Identify what to protect.
- Develop an inventory of all the firm’s hardware.
- Catalogue all software including licences, versions and passwords.
- List all online services that the firm uses.
- Evaluate all vendors’ security systems.
- Analyse the risks.
- Understand the regulatory requirements.
3. Implement advanced security measures
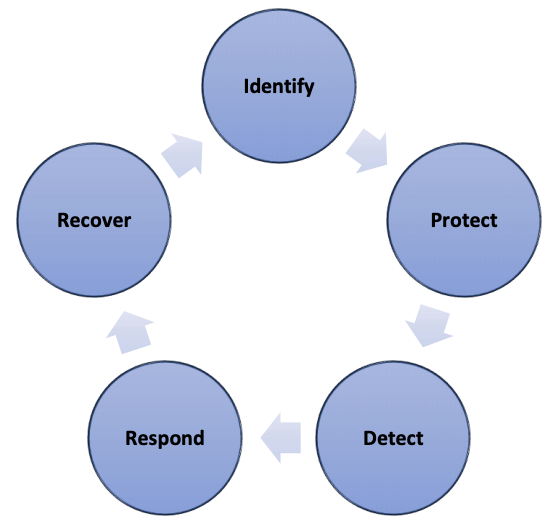
- Identify the vulnerabilities in the system and implement risks controls.
- Protect the system against threats whereever data resides or is accessed, e.g., cloud, BYOD devices and any place where users may access the network.
- Detect by conducting frequent network monitoring.
- Respond quickly to threats to minimise damage.
- Recovery preparedness must encompass restoring affected systems and eliminating the security threat.
4.Develop policies and educate employees
Train all employees regularly on data protection legislation and the firm’s cyber security policies. They need to be able to recognise red flags and know how to respond to a security incident.
5. Prepare with crisis response plans and don’t just focus on the technical
Have in place an action plan that deals not only with the technical processes (data breach management/business continuity) but also how to communicate proactively and transparently with stakeholders.
Knowing how to handle traditional and online media is important as they all play a vital role in how the firm is perceived internally by employees and externally by clients and the general public.
6. Cyber insurance
Consider purchasing cyber liability insurance policy for the firm. Having a cyber insurance plan in place could save the costs of consultants, new equipment, marketing, and other associated expenses in the event of a security incident.
Implement Data Security Measures – Do IT Now
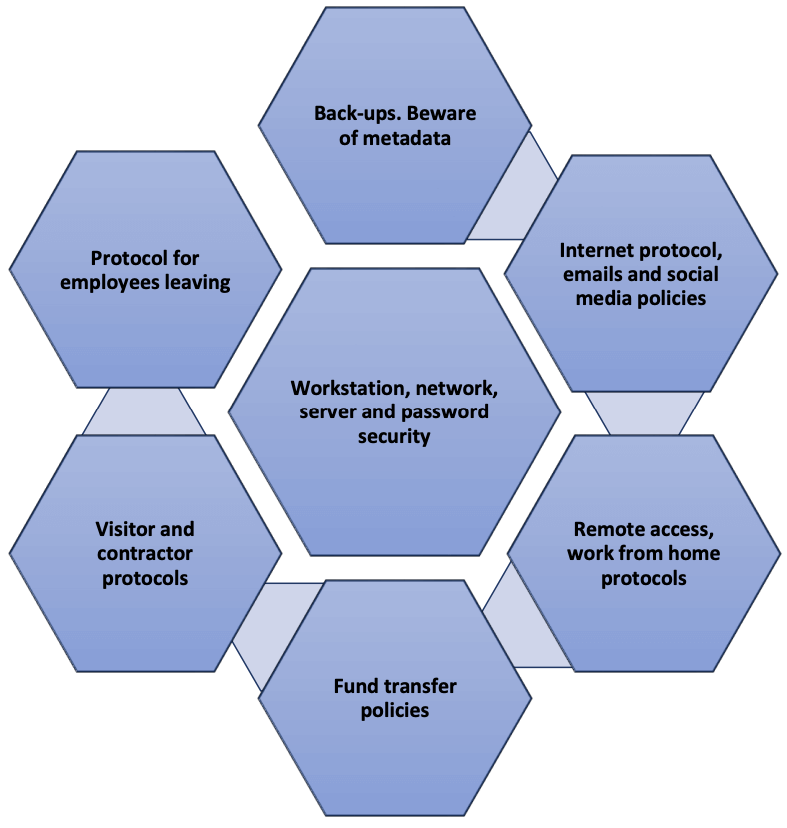
1. Workstation, network and server security
- Restrict who has the right to download files / programmes and modify items in certain folders.
- Deploy, maintain and update anti-malware.
- Conduct regular systems assessments and penetration tests.
2. Password security
Ensure that system passwords for wireless access and other equipment are strong and changed regularly.
3. Backups
Budget is often a factor in deciding a backup system, cloud USB or tape. There is no value in choosing a backup system that requires tedious work (that never actually gets done) resulting in not having a current backup when needed.
4. Metadata
An often over looked data security danger is metadata contained in document editing programs. Files sent electronically should be scrubbed for metadata.
5. E-mails4Refer to the Law Society’s Guidance Note 6.1.1 on emails.
Train all employees on how to open and read email headers for signs of email spoofing or phishing.
Discourage employees from personal use of the firm’s e-mail system to conserve server space. Sending a free birthday card from a website may introduce massive spamming into the system.
6. Internet use
Have a clear internet acceptable use policy. This will mitigate the risk of employees inadvertently or maliciously transmitting clients’ or law firms’ proprietary information.
7. Social media
Develop a social media policy.5Refer to “Defining Your Social Media Policy” Singapore Law Gazette July 2017 for guidance on how to develop a social media policy. Be vigilant when using social media as it may contravene professional and ethical obligations, including obligations under the PDPA. Employers can be held vicariously liable for their employees’ social media use, for example, if confidential client information is disclosed, or if personal data is disclosed in breach of the PDPA.6Refer to the PDPC decision in Executive Coach International Pte Ltd (2017) SGPDPC3.
Personal postings on social media could be interpreted as representing the views of the law firm. Online activity that can be traced back to the firm’s domain are ultimately linked, whether or not the firm is mentioned.
8. Fund transfers
Following the two reported scams in April/May 2019, the Law Society of Singapore has advised lawyers to:
- advise clients who receive email requests regarding fund transfers to verify with the law firm before effecting any payments.
- clearly communicate payment instructions to clients who are not IT savvy.
- explain conveyancing processes and timelines clearly, preferably in writing, to foreign clients and permanent residents who are unfamiliar with such matters.
- advise clients to re-confirm with law firms before taking action, especially if clients receive instructions that deviate from previous communications.
9. Remote access/Work from home protocols
Two of biggest exposures when working from home or remotely are devices and internet connection.
When lawyers work remotely, they may access sensitive data from unsecured locations. When they use their personal devices, they operate outside the firm’s IT parameters and expose the firm.
Ensure that information stored on, sent to or from remote devices is properly safeguarded with encryption or multi-factor authentication. Smartphones and tablets should have to input passwords at both starting-up and before leaving screensaver mode. Develop a remote wipe program protocol for lost or stolen devices.
Avoid using ”free” and/or unknown wireless services to access the firm’s e-mail or practice management system. As far as possible, use mobile data service. Alternatively, consider using a virtual private network (VPN) which will encrypt any traffic through the hotspots.
10. When an employee leaves
Develop a process to manage electronic access to the network when an employee resigns or is terminated. A disgruntled or exiting employee can easily delete files from the system or take files out of the office without notice.
11. External contractors and visitors
Have in place a confidentiality protocol for system contractors carrying out system updates and maintenance as they may access confidential information in the process. Any temporary account established for office visitors should have a notice regarding expectation of privacy. Passcodes for these accounts should expire immediately after use, to ensure the office visitor will not be able to access confidential data later.
Don’t be the Next Victim
It is crucial for law firms to have robust cybersecurity strategies to avoid becoming the next victim. Malicious actors are constantly engineering new ways to steal, corrupt and disrupt business operations through unauthorised access to sensitive data.
Most data security measures focus on external threats from hackers and malicious downloads. Internal threats are equally common and dangerous as they are often the result of intentional or unintentional problems created by employees’ use of software and equipment. Mitigate employee related risks by testing their security acumen in simulated phishing attacks. In addition to basic cyber hygiene training, ensure role-specific training for employees who have higher access to information.
Data risk management is not solely the responsibility of the IT department. Senior management needs to take overall responsibility with support from every department in the law firm.
Review the recommended security measures set out in this article, go through the e-learning programme on data risk management and the other resources available in the Law Society of Singapore’s Risk Management Portal. Refer to the Law Society’s Cybersecurity Guide for Law Practices7Refer to the Law Society’s Guide to Cybersecurity for Law Practices (30 March 2020) on how to strengthen cybersecurity resilience and keep information safe and secure. Then take steps to assess your system vulnerabilities and implement mitigation steps.
Don’t be the next victim.
Endnotes
| ↑1 | Matthew Chiong Partnership (2019) SGPDPC (7). |
|---|---|
| ↑2 | Refer to PDPC’s Guide to Preventing Accidental Disclosure When Processing and Sending Personal Data. |
| ↑3 | Guide to Developing a Data Protection Management Programme.Refer to the PDPA Assessment Toolkit available on the PDPC webpage for guidance on how to conduct data protection risk assessments and implement risk mitigating measures.Also refer to “Why you may need a privacy policy” The Singapore Law Gazette June 2017 for suggestions on how to develop a privacy policy for your law firm.Refer to the Law Society Guidance Note on cloud computing (paras 12,13,15,16 & 17). |
| ↑4 | Refer to the Law Society’s Guidance Note 6.1.1 on emails. |
| ↑5 | Refer to “Defining Your Social Media Policy” Singapore Law Gazette July 2017 for guidance on how to develop a social media policy. |
| ↑6 | Refer to the PDPC decision in Executive Coach International Pte Ltd (2017) SGPDPC3. |
| ↑7 | Refer to the Law Society’s Guide to Cybersecurity for Law Practices (30 March 2020) |